Tabnabbing: A New Type of Phishing Attack
The web is a generative and wild place. Sometimes I think I missed my calling; being devious is so much fun. Too bad my parents brought me up with scruples.
Most phishing attacks depend on an original deception. If you detect that you are at the wrong URL, or that something is amiss on a page, the chase is up. You’ve escaped the attackers. In fact, the time that wary people are most wary is exactly when they first navigate to a site.
What we don’t expect is that a page we’ve been looking at will change behind our backs, when we aren’t looking. That’ll catch us by surprise.
How The Attack Works
- A user navigates to your normal looking site.
- You detect when the page has lost its focus and hasn’t been interacted with for a while.
- Replace the favicon with the Gmail favicon, the title with “Gmail: Email from Google”, and the page with a Gmail login look-a-like. This can all be done with just a little bit of Javascript that takes place instantly.
- As the user scans their many open tabs, the favicon and title act as a strong visual cue—memory is malleable and moldable and the user will most likely simply think they left a Gmail tab open. When they click back to the fake Gmail tab, they’ll see the standard Gmail login page, assume they’ve been logged out, and provide their credentials to log in. The attack preys on the perceived immutability of tabs.
- After the user has entered their login information and you’ve sent it back to your server, you redirect them to Gmail. Because they were never logged out in the first place, it will appear as if the login was successful.
I dub this new type of phishing attack “tabnabbing”.
Targeted Attacks
There are many ways to potentially improve the efficacy of this attack.
Using my CSS history miner you can detect which site a visitor uses and then attack that site (although this is no longer possible in Firefox betas). For example, you can detect if a visitor is a Facebook user, Citibank user, Twitter user, etc., and then switch the page to the appropriate login screen and favicon on demand.
[*] Think looking for the exact error thrown when embedding <script src=”http://gmail.com”/> it will be differ depending on if the user is logged in or logged out.
Even more deviously, there are various methods to know whether a user is currently logged into a service. These methods range from timing attacks on image loads, to seeing where errors occur when you load an HTML webpage in a script tag*. Once you know what services a user is currently logged in to, the attack becomes even more effective.
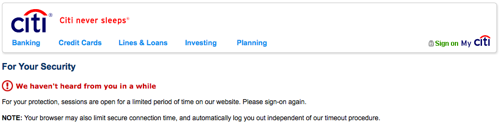
You can make this attack even more effective by changing the copy: Instead of having just a login screen, you can mention that the session has timed out and the user needs to re-authenticate. This happens often on bank websites, which makes them even more susceptible to this kind of attack.
Attack Vector
Every time you include a third-party script on your page, or a Flash widget, you leave yourself wide open for an evil doer to use your website as a staging ground for this kind of attack. If you are the evil doer, you can have this behavior only occur once in a while, and only if the user uses a targeted service. In other words, it could be hard to detect.
You can also use a cross-site scripting vulnerabilities to force the attack to be performed by other websites. And for browsers that do not support changing the favicon, you can use a location.assign call to navigate the page to a controlled domain with the correct favicon. As long as the user wasn’t looking at the tab when the refresh occurred (which they won’t be), they’ll have no idea what hit them. Combine this with look-alike Unicode domain names and even the most savvy user will have trouble detecting anything is amiss.
Try it Out
You can try it out on this very website (it works in all major browsers). Click away to another tab for at least five seconds. Flip to another tab. Do whatever. Then come back to this tab.
It’s hard to find, isn’t it? It looks exactly like Gmail. I was lazy and took a screenshot of Gmail which loads slowly. It would be better to recreate the page in HTML.
Update: Many people have reported that the attack doesn’t change the favicon in Chrome. This was due to a bug in Chrome which has been fixed in the version 6.0.408.1. Chrome is fully susceptible to this attack.
You can get the source code here: bgattack.js.
The Fix
This kind of attack once again shows how important our work is on the Firefox Account Manager to keep our users safe. User names and passwords are not a secure method of doing authentication; it’s time for the browser to take a more active role in being your smart user agent; one that knows who you are and keeps your identity, information, and credentials safe.
19543 ♻ Retweet | Follow @azaaza on Twitter | All blog posts
No related posts.




eli
In the latest mac chrome, the inactive tab’s favicon doesn’t update. other than that, this is flawless and insidiously genius.
Kal
Hmm it did for me, although I’m using nightlies at the moment :O
and yea this is rather evil :)
Té
In the latest Chromium nothing changes. Favicon, title and page content remain the same.
Favicon changing doesn’t even work on active pages. :-/
http://ajaxify.com/run/favicon/scroll/
Tobu
Does too. I’m running 6.0.414.0 (48010).
Ross R
Same here – latest PC Chrome Beta – the favicon doesn’t update.
Angus
There’s a slight difference between Chrome and Chromium ;)
Chromium Dev on Ubuntu seems to be immune – for me at any rate.
Ross R
Oh – and the vimeo video stayed up on top of the gmail login screen image
Sebastian Campbell
hi
Sebastian Campbell
AMAZING STUFF
Rafael
Another reason to use a mail client.
Simon
@Rafael – you’re missing the point. Yes, a local mail client protects you from the GMail example, but the trick works on *any* web site or application. Facebook, E-Bay, even your banking site…
Dave Winer
Using an email client to browse the web does protect you. This is how Richard Stallman uses the web: http://lwn.net/Articles/262570/
Aza Raskin
But that doesn’t work for most modern sites. Can you check your bank via Richard’s mail-proxy?
evan
RMS solves that problem by not having any money.
Simon
Except that his view of the web must be a very limited one. That trick certainly won’t work for any interactive site (not that RMS is likely to be a Facebook user), nor presumably any that requires authentication like a banking site. It probably rules out commenting on any blog that requires a captcha.
Really, if that claim by Stallman is true, I really wonder what his view of the world is like, given how important (for better of worse) the web has become to social interaction these days…
Sergei
I would argue email clients can be significantly worse in another way — most popular email clients like Outlook and Thunderbird don’t encrypt passwords and other sensitive information, sending it all and receiving as plaintext.
And as others have said, rms is a special case, and it is ridiculous to browse the web in that manner for anything meaningful. It works for him because he doesn’t give a shit about anything except a few pages he bookmarks for later.
Rafael
There’s another way to browse the web in an email client…
Rafael
@Simon – I’m not missing the point, I was just making another one. I know. There’s nothing consistent with authentication especially with permanent cookies and session timeouts. So at a banking or investment web site, it’s possible to do this attack. The point is that with clients like an iTunes or mail client is that you know what you’re logging into, so this wouldn’t be possible in that environment.
Brian Shumate
Nice discovery!
FWIW, I tried this in Chrome 5.0.375.55 beta on OS X, and the tab title changed, the page content changed, but the favicon did not. Same behavior for Opera 10.10, too…
Mike Grace
Holy Cow! That’s creepy! Tried it in Chrome on Mac and it didn’t work. Thanks for sharing so I can keep an eye out.
Aza Raskin
It appears that Chome/Safari doesn’t allow you to change the Favicon easily. There’s probably a hack, though.
Tiago Sá
This is why it’s so important to develop appropriate session/login technology like Opera’s Magic Wand or the proposed Firefox 4 session manager. Hopefully we’ll see some improvement from that in the future.
Aza Raskin
Absolutely. I’ve added that as a pointer to the Account Manager at the end of the post.
Tiago Sá
Also, extension-ridden Firefox 3.6.3, the favicon doesn’t update. I don’t think that’s a good sign :( I will try to see which extension is causing this problem.
David
If you have Favicon Picker installed and enabled, that’s probably it.
tom chiverton
Mostly works on the Firefox-derived Microb browser on Nokia N900 smartphone too. Just don’t image load till swap back to page. could easily be written off by user as graphical glitch !
Simon
Huh, that is indeed rather devious.
Seems to me that this is where some of those ideas of “Application Tabs” in future Firefox would help too – the lookalike will stand out a bit more if the user is accustomed to their GMail or Facebook tabs being ‘special’.
brian krebs
Very nice post.
just a typo nit (i’m asking for a fix b/c i’d like to quote you:
“As the user scans their many open tabs, the favicon and title act as a strong visual cue—memory is mailable and moldable and the user will most likely simply think they left a Gmail tab open”
….you probably meant “malleable”.
Aza Raskin
Thanks for the typo find. Fixed.
@laura: I fixed yours too.
laura
Also prays should be preys. :)
xoxo,
fellow grammar snob
skierpage
Whooooa.
So users need to click the website chrome icon and click [More information...] and verify before entering anything sensitive in a tab?! The inspector Larry identity doorhanger (I think that’s its name) should probably have more info than “This web site”, it should have the original icon and site name.
Té
You have an urlbar, don’t you?
UncleZeiv
Actually, Vimperator users don’t (but they should have the URL displayed on the status bar).
Francisco
So… you tell and warn us about this type of phishing, and then publish away the core script for anyone to use?
When described is not hard to do it, but still…
Francisco
Forgot to mention. On safari 4.0.5 (mac) favicon doesn’t change.
Aza Raskin
There’s always a fine line between disclosure and holding back. My gut feel in this case was that (1) given the description it is easy to implement, and (2) the demo would easily be view-source-able. Thus, I disclosed the source.
Rizwan ud Dean
this does not work with the Google Chrome Browser.
Laneth Sffarlenn
Dude, that is just not cool – going to tell everyone I know because that is just too scary.
Eric
Yeah, this definitely highlights the need for an alternative to the standard login/password security model.
Just off the top of my head, if asking for a username and password became the exception rather than the norm for sites across the web, only used to install a cert or similar on one’s computer a la Kerberos, people would be more suspicious/cautious when a computer that they previously authorized suddenly asked them for their credentials.
No idea how one would get that movement going without having a phishing pandemic across the web to motivate it, though.
Agustín Amenabar
In Chrome the favicon doesn’t change, but the image does, and I didn’t look at the address bar.
Then I tried in firefox, it is scary.
In Opera the favicon doesn’t change also.
this is scary.
thanks.
Té
The animation works in Opera 10.53 here even when the tab is not focused, so there ought to be a way to work around that.
http://ajaxify.com/run/favicon/scroll/
Adam Shannon
It would be even better to detect the “most valuable” site that a user has visited (with your Social History Script), then grab the html of that site’s login page and alter the form’s action [and method] property(ies) to send the data to your page.
Another layer, once you get the info for one site set a cookie so you don’t ask for the details again (at least until the login fails).
That way you can grab multiple accounts from each person and you’re assured that any changes to the layout is concurrent with the phishing page (barring any changes to the form (I’m thinking of getting the form via JS.)).
How to combat, install a plugin/extension/addon/GM script that captures a screen shot of the page onload, then compare it to the site just before any form submission and see if they match.
Or, monitor any changes to the document’s code base and if a reasonably large set of changes has occurred then warn the user and stop form submission. (Also, you can have the extension send a warning email to the site owner(s).)
Just some thoughts.
Aza Raskin
Adam, those are some excellent and devious ideas. Being able to go after multiple accounts with a single page is a fantastic (and scary) idea.
penguat
To refine the attack, you might be able to redirect in the background to a lookalike url as well?
I’m more than a little frightened by this one…
Jason
Wow, that is scary. There’s a high chance that I would fall for something like that.
celina Lee
Very insightful!
johnjbarton
Hi Aza, the part I did not understand was the “Every time you include a third-party script on your page…”. I guess this is not literally true? If the 3rd party is trusted and the script is included via https, how there still be an attack?
jjb
Aza Raskin
Not exactly. When you include a 3rd party script, you are explicitly giving the ability for that site to run arbitrary code on your page. If you are using a service via inclusion of a script tag (think ad networks or web analytics), and that service turns evil or gets compromised your website can now be an attack vector.
Adam
Have to note here that I was using a (web based) blog aggregator and was quite surprised to see a gmail login page when I returned.
Adam
But jjb is right, if you *trust* the 3rd party, you are assuming they won’t be evil or they have good enough security.
I wasn’t fooled by this because I always login to a site after opening a new tab, never through an existing one. Also, I check to see if the url is https and the correct domain. Not so for someone who isn’t so webby..
voracity
Certainly a neat attack, and very evil.
Anyhoo, callback logins would also solve this problem. i.e. Instead of a username/password, the site sends you an email (or instant message) with a one-time login link.
grabur
I’d like this method to replace, chip and pin. Text a code to your mobile. As long as the text didn’t get held up, it would be a great way to authenticate you, except that is if a thief stole your mobile, got your pin and bank card! I.e. stole your computer.
grabur
A concern about this kind of method, is something as stupid, as when I click on a link in my im client, I might want to open it in a different browser to my default. Or what happens if I’m on the console? Could be rectified in the os.
Tim
The demo attack didn’t work on Chrome. Had to switch to Firefox to witness this vulnerability.
Vince Maniago
Genius Aza! You should have been a bank robber.
Ray Pettersson
Great article Aza! Nowadays, learning how to identify phishing site is becoming another skill we need to have to safely surf the web. Thanks for sharing!
Hal
Either I missed something, or there’s another point that hasn’t been brought up.
What if the user has his username and password automatically entered for a site? Say I have that done for Facebook, I visit an infected page, then go to another tab, and it mimics FB and asks for my login info.
As I understand it, since it only looks like FB, but the url is not FB, it won’t enter my login info, which should be a clue to me.
But if I really am missing something and it not only mimics FB, but also can alter the URL so Firefox thinks it IS Facebook (when it isn’t), then my username and password will be entered into the form automatically. If that were the case, a little Javascript code could detect my info in the proper fields and send that anywhere, without me ever knowing about it, then it could change back to the page it was originally, leaving no clue at all anything had happened.
Leszek
Don’t worry, that can’t happen.
Hal
So if the URL can’t be forged, then any program I’m using to remember login info would not be fooled, right? So if I follow a simple rule of not re-entering information for sites where my login info is stored, that would keep me from falling for this? (Of course, now I’m going to check the URL before entering any login info for re-logging in, but am I right about that?)
Maybe I’m anal, but I tend to arrange my browser tabs to match my browsing habits. I have one window that’s always up with the news sites (and XKCD) that I visit almost daily. If a favicon popped up that was out of order, I’d see it. Then I open other windows when I’m doing specific tasks and keep related tabs together. I wouldn’t for example, have any banking sites in a tab in a window with other types of sites. I also keep track, in my head, any time I change focus from a secure site I’m logged in to (usually I log out rather than switch to other tabs). That doesn’t make me immune, but it does help me know what tabs are where.
Tobu
> So if I follow a simple rule of not re-entering information for sites where my login info is stored, that would keep me from falling for this?
Using a password manager helps (also consider “secure login” fore firefox), but there is a misguided tendency in ‘critical’ sites to ask the browser not to retain the password.
Blake
As far as a “misguided tendency in ‘critical’ sites to ask the browser not to retain the password.”
For me, I don’t allow it to remember my online banking password as well as PayPal. My thoughts are to avoid having a computer thief just walking right in to these accounts if my computer was stolen. Is this “misguided”? I would really like to hear your opinions on this.
Ted
Woah. I opened several articles at once, queueing them up to read, and when I got to yours for the first time, closed it thinking it was Gmail. Only after coming back did I realize what had happened..
..that is just too effective.
starwed
This totally got me too.
Michael Chui
Suggestions for increasing savviness:
1) Check the URL before you enter login credentials, always.
2) Don’t leave open tabs to things you need secure. I never have a tab open to a bank’s page unless I’m browsing as a visitor. If I see a tab asking me to log into my bank account, I didn’t leave it open and it’s fishy.
3) Tabs that you do leave open, try to keep them in one place. All of my “check them constantly; refresh often” tabs are on the left. If a tab is out of place, then something is screwy. There is no way to programmatically alter tab arrangement yet.
grabur
While the URL check is good, I’m sure not many people check them, and I wouldn’t be surprised if they were hidden in later browser iterations. Plus I wouldn’t put too much faith in the address.
Kerberos
You sir…are a genius. I am thoroughly amazed at what you have come up with. Incredible. Very nice work :)
mrb
Impressive type of attack, Aza! One way to defend oneself against it is to use 2 browsers:
http://blog.zorinaq.com/?e=13
Fred
A mechanism to group tabs (I am sure Aza could come up with something ;) ) that puts specific tabs into a specific group automatically could also help this. For example (just thinking out loud here), if every time you visited your bank, that’d switch your view to the “trusted” group and maybe even adjusted the Persona appropriately, then you’d have strong visual hints about the authenticity of the site. You’d know: My bank can’t, ever, be shown with the Harry Potter persona, but only with the Hello Kitty one.
Aza Raskin
Fully agreed :) Having semantically related tabs in groups would help you figure out when a tab was matching its surrounding tabs.
Laurian Gridinoc
This recalls me of Tyler Close’s http://petname.mozdev.org and on a group of tabs that would be interesting
Sam
Great work Aza! At times I am very tired and may input the password now I see the importance of Roboform.
P.S _ Your comment box is beautiful , is it the script you made?
Aza Raskin
Thanks, Sam. Yes, the comment feature is a home-spun script. Perhaps I’ll write a blog post about how I wrote it?
grabur
Interesting attack vector, If you hadn’t used an image, you’d have got me!
This further accentuates the need to re-think the web browser. All the browsers are soo 5 years back.
X
ever thought about what toolbars do?
Parashuram
Hey,
There is a similar attack vector against Google Gadgets and the attack on Google Wave is a classic example. Here are the details – http://blog.nparashuram.com/2010/02/phishing-with-google-wave.html and here is the video … http://www.youtube.com/watch?v=luHo8gz_o48
p0deje
why not do document.location to simply change URL? do you think user would notice loading site?
Aza Raskin
I doubt people would notice the loading site. We could use this technique for browsers where it was impossible to change the favicon on-the-fly.
treeofpain
so many sites cross-script for ads, that a forced refresh loading more rubbish (or that simply never finishes), would probably be never noticed.
Wolfgang Hospital
This description presumes script evaluation enabled – more often than not, I don’t even allow loading of images before a URL check and/or a peek at the frame/page source.
Reminds me: how about marking “allow” exceptions with “just this session” or an expiration?
(haven’t tried using a “block”-list)
Regards
Diogo Gomes
Chrome doesn’t allow you to change the favicon.
Try this page on Chrome and you will see.
Diogo Gomes
Oops, nevermind, didn’t see the other comments.
Anyways, since favicons are very important for Chrome they don’t allow you change it to prevent stuff like this.
I think they were targeting other methods of phishing (iframe?), glad it also works for this method.
starwed
It doesn’t really completely block the attack. If you happen to end up on the tab without looking at the icon, they’ve still got you.
Aza Raskin
Also, you can just change the location of the page behind the scenes (i.e., location.assign). If the user misses the page load—they’ll be focusing on the tab they are looking at—when they come back they’ll be looking at a perfect Gmail impersonator.
Svoop
I’m relying on 1Password (Mac only though) to manage my passwords and as this attack method doesn’t rewrite the page location, 1Password won’t fill in my credentials in on the phishing screen.
Mansoor Ahmed
Indeed, it is very shocking! but I dint get the point from where this attack originated :(
Dan Dart
Really teaches you to /look/ at your URL.
Corey Ballou
Very interesting attack, indeed. The favicon is the real kicker here. The only way I could tell was from the address bar. Guess I’ll just have to heighten my senses for awhile.
Nikke
Wow. Nice and very evil. Although, in my case it wouldn’t have worked.
I’m using a script (bookmarklet) as my aid to not reuse the exact same password on any two websites. It uses a secret salt + the current domain to mutate a base password into a unique password for each website.
So, for me, even if I would fall for such a scam, it wouldn’t do much harm, as the result would be useless. But that’s just me, Joe Surfer probably isn’t as paranoid and/or tech savvy as I am.
Tobu
Not really, your keystrokes could be logged via javascript before the bookmarklet encodes them.
Nikke
This is true, but as I’m using a salt to mutate the password, even if I tell you my password, it will still be useless to you.
Ricky B
I have changed yours a bit. Instead of pulling the image from a remote file I have used data:image/png;base64 to store the image in the .js file just on the off chance the hosted image goes down or can not be accessed.
Only real trade-off is size/lines of code.
RB
Gareth
Well, a real attack wouldn’t use an image, it would construct a form that actually submitted somewhere. You can’t collect login details with just an image
Ricky B
I am aware was more a change for the example code.
Just to make it more self contained.
Dagmar
Works on Chrome
Laurian Gridinoc
What if Firefox would recall sites (and their favicon) you log in into, and when on another domain you get a known favicon you would get a warning.
Now, computing favicon similarity would be tricky, the pixel space is quite small… and I bet that you can have significantly different favicons that look almost the same for the user.
Jörn Zaefferer
The GMail example is particulraly creepy as GMail logs you out randomly every once in a while, even with the browser staying open all the time.
Sidenote: Your sidenote gets screwed when reading this in a RSS reader (eg. Google Reader). The sidenote text appears before the paragraph where it is referenced.
alex
Now if this works on mobile devices, its gonna really be awesome and deadly!
Shouldn’t be hard to tweak it… ;-)
Axioplase
I suppose that firefox can know the pages I navigate too, including those that need a login/pwd.
I suppose too that it is capable of rendering a web.
I suppose also that it could store the rendering of the login pages I use, and compare them to each tab I navigate too. Should two renderings be similar (via some comparison function on pictures that does not have to be extremely precise), but the corresponding websites be different, you would trigger a phising alarm.
Considering how geniously tricky this hack is, I believe that a solution like the one I just made up and suggested could then block quite a number of such attacks.
P!
evan
but comparing every site you visit with every other site you visit (or even just most sites you visit) is computationally expensive, and it would likely be trivial to get around (simply add HTML that renders invisibly, or build the page in a novel way, or change the layout slightly). Heck you could probably just change the page’s layout dramatically and 90% of the people out there would probably not notice.
Bla
Nothing happened on Google Chrome.
Clark
If you use PasswordMaker, it’ll use the domain of the website to generate the password for you — so, although you’d sign-in, they wouldn’t get your password.
Mr. Tarpee, Gym Coach
FYI: AdMuncher prevented any of the malicious script from executing.
Don’t get all up in those interwebs without proper protection, kids!
evan
ok but you could conceivably perform this hack with a refresh.
Dmitriy
Linux:
Chrome: Does not update favicon or page.
Firefox: Does not update favicon or page.
mlok
NoScript blocked this attack.
(I’ll desactivate it so that I can check it out anyway)
WhtFk
Brilliant – thanks for sharing… Completely agree an additional authentication layer for browsers needs to be established.
In the meanwhile, Im going to hijack all of the social media and bank accounts I can – cheers!
FrancisT
Those of us who use the “noscript” plugin are not affected unless we’ve enabled support for the site and/or 3rd party ad shower in question.
Sure if the site itself is evil then we have no protection but if its the ad network then – assuming we blocked the ad network and that is probably the main reason for running noscript – the attack fails.
Klaatu
I have seen this “out in the wild” a few times already. Rather than phishing for logins, it just changed the referrer page to another page, I guess for the click count. Once it even cascaded down through several referring pages, changing almost everything I had open. And of course the back button did nothing. So phishing is just one aspect of this. Is there any way to stop this behavior short of not allowing scripts to run at all?
Phaenotyp
I tried in IE 8, FF 3.6.x, Safari 4.x and it worked. It didn’t work in 4.1.x of Chrome.
Pål
Me and a friend was talking about this issue on MSN just now, and it’s a real headache to fix this for browsers.
Everything suggests that DOM-tree manipulation in inactive tabs is a wanted feature for browsers. Preventing inactive tabs from using javascript is not an option. Think only of the implications that would have on Facebook Chat, Gmail, and numerous other high profile features.
So what can be done to prevent this? Very little, I imagine.
However, there could be some browser design changes made which could help the user identify such pages.
We suggest a feature where a visual snapshot is taken from tabs when they go inactive. When a user navigate back to the tab, the snapshot is displayed for a predetermined time, lets say 200ms or whatever looks best, and then the updated visual fades in. This would alert the user if the change is major, and really wouldn’t bother the user if all that’s changed is the email list or the chat window. In fact, it could be a visual cue as to whats changed and considered a feature.
In addition there could be displayed some form of visual cue on the tab or somewhere else in the browser if the DOM-tree had changed “while you were away”.
This should of course not be applied for video, flash and other such interactive media.
Tobu
That fade-in idea sounds good.
Other options: blocking background tabs from doing favicon changes, title changes (though that would kill Gmail’s message count), location changes.
Consider flashing the tab instead so that notifications still work. Web notifications are still available for more fine-grained legitimate uses: http://dev.w3.org/2006/webapi/WebNotifications/publish/
And there’s the option of blocking favicon changes (and long animations) entirely.
Pål
Also I forgot to mention, the fix proposed in the original blog post is not really a good one. Firstly it assumes everyone use or want to use such an extension, and secondly I think it’s a wrong attack vector as it doesn’t directly alert the user of the problem.
abickford
Very clever. However, it doesn’t seem to work in Chrome and IE doesn’t replace the Favicon. Then again, I doubt most IE users would notice ;)
I don’t have safari/opera so no idea how well those fare, but according to the comments of the favicon script it should work on opera as well.
Qinoi
Works in Opera.
But this kind of trick doesn`t affect any built-in password manager.
Simakuutio
Well… seems to be working with Opera too (10.53 tested)… so this affects to quite many people regardless which browser they are using….
Don Synstelien
It’s not just a Javascript that is a problem.
I rail against Flash all the time because unless you specifically block a flash embed from allowing Javascript execution, a .swf embed will allow whoever hosts it to change functionality on the fly without giving any indication to the person who embeds it. In effect, you could build a widget that looks useful… Say, a Twitter widget, and get a wide enough audience and you could then do this from other peoples sites remotely.
At least with a .js only solution you can usually ferret out what scripts do or where they point. with flash it’s all hidden from view and pretty much completely undetectable until the malicious hacker plans to launch an “attack”.
Take a look at my linked in profile to see why I might have insight into this.
Marc Grondin
Ok this is a little scarry…but i do notice that the address in the address abr does not change to the gmail address so in fact it is verry easy to notice that you are not at gmail. can javascript change what is in the address if not then this really should not get anyone as you only have to pay attention to your address bar and you will see.
Marc Grondin
also in chrome ver 6.0.408.1 DEV it does not work at all…
Erik van Eykelen
A possible effective counter measure would be to 1) count the nr of DOM elements when a user *leaves* a tab (e.g. clicks on another tab or opens a new tab) and then 2) warn the user when more than 10% of the DOM has changed when the user returns to this tab. “Counting” should be less naive than simply counting DOM elements because the hacker can balance this but you get my drift.
Tobu
You could use images or flash and change very little of the dom.
Erik van Eykelen
A hacker needs a couple of text fields to grab your information, either via an html form or Flash app.
In all cases this means the hacker has to inject some HTML or make some hidden elements visible.
Such changes in the DOM can be detected by a browser plug-in. This plug-in would provide the counter measures for this type of attack.
Tobu
Another thing to consider: the attack could already be in the DOM, and enabled by tweaking opacity or z-order, using animations, css transitions, probably more.
I don’t think a defense that tries to “see” the page like a user does is realistic, because the relationship between document structure and user perception is very complicated (and because there are more reliable ideas in-thread).
blake sisco
ok…correct me if I’m wrong…I’ve tested this in Chrome 6.0.408.1 dev (PC) and it works. I’ve also tested in IE 7/8. The only thing that doesn’t work is the favicon. Theoretically the attack is still successful, correct? The image changes and the window/page title change but the url stays the same. Doesn’t the favicon just serve as another tool in the deception of the user?
J
In Chrome, the favico doesn’t actually change, which makes it a bit of a giveaway.
blake sisco
That’s odd my build changes the favicon…
Jope
My build (Chrome 6.0.408.1 dev) changes the favicon as well.
BTW Chromium says there’s nothing to fix:
http://code.google.com/p/chromium/issues/detail?id=45008
tewo
average user will probably fall for it, but i’ll definitely notice the address bar even if this attack gets past NoScript
Etc.
It works on Chrome, when you open another window (not tab).
WebDevHobo
At first I was thinking: nobody can be that stupid.
But then I realized I was talking about people on the internet.
John
Hello,
I notice the link for the Firefox Account Manager does not load (it just keeps trying and trying).
I looked on the Firefox Addon site and still no clues.
It is still there or did they change the name.
Got a plan B program to use?
Thanks,
John
timóteo
Scary o.o
Using something like lastpass wouldn’t be just like the account managar you talk about?
I never type my passwords anymore because of it.
Staffan S
I don’t know if this remedy was already suggested: reprogram the legit site to always respond to a succesful login with an individual secret word or sentence, submitted by the user upon registration. If the user does not see his/her expected words, its a phishing site. A little cumbersome but still.
evan
Easy to get around. The attacking site captures the victim’s username and password, logs in to the site using the legit info, and gets the user’s verification image or text.
Most users never actually pay attention to that stuff anyway.
davey
The username password forced logout is the vector here, as users are trained into treating the relogin as annoying thing they have to do.
FYI Sites which use an personal identification image like BofA would be much less likely to be affected as they can spoof the page layout but not the private image.
Sam
This is what I was going to mention. Sites that use a private image that only the original site knows, won’t be effected by this attack. Which is why I think all secure logins should have some form of a private image.
Julius
scary concept. does not seem to work in chrome though, no idea why…
intel_chris
Actually, this attack looks pretty effective in my chrome browser. Sure the favicon and address bar aren’t correct, but when I navigate away from chrome altogether and come back, it looks (at first glance) like I need to log in to Gmail. Since I’m often tired and inattentive while using the computer, that could be enough under the right circumstances. It almost fooled me the first time. I’m sure it would be enough for some people and that’s what phishers are counting on. They don’t care if they catch everyone, they just need to land enough phish.
Password and re-logging-in schemes are dangerous. They do train users to give away info.
rage
This is ridiculous. First of all, I was able to see the transition in progress while the page was still open because of a tiny IM window that popped uup which removed focus from the tab. Even the dumbest users wouldn’t trust something they just say mutate into something else.
Another issue, the biggest flaws actually, is how the hell would you know they have a gmail/hotmail/etc to trick them into logging into in the first place? Say the tab tricks them into thinking its chase’s website. Maybe they don’t even USE chase. People don’t just log in to ANYTHING. Current phishing methods know you use the target fake site simply because you clicked on the link. How? Because the email could say “from chase, blah blah please update your email blah”. Only people who USE CHASE would even click in the first place. How would you randomly guess a site to fake if you don’t know what sites the user uses? Answer: you cannot. You just guess.
Too many issues with this “new method” exist for me to take it seriously.
You’d have to pray the user didn’t notice the “transition” occurring. In addition the faked site would have to be something that they would log into in the FIRST PLACE. This is a monumental guess seeing as there’s no way to know what sites a random user actually uses.
Anonymous
@Rage: Does it also amaze you that spam works? Spray and pray baby, just spray and pray.
Quentin
@rage see @AdamShannon’s post above – script could scan for most valuable sites.
I might suggest also making the attack wait until the entire window lost focus and/or was pushed to the back. Not sure if expose events are accessible from scripts, but once you have an exploit like this in place, the attack vectors will get better and better.
Concerned User
Hello Aza: Thanks for posting this and keeping everyone informed! Noscript blocks it out….To test this out, I disabled it and the favicon changed:(…
Oh! I think that this attack would not work if there was another addon like secure login which saves credentials for a particular site. Of course, the phish page would look too genuine and the user would think that something was wrong with the addon and provide the credentials:(….
No one would care to take a look at the address bar!
Tobu
Have you considered blocking favicon changes from the DOM, as well as animated favicons that take more that one second to cycle?
Gonware
good!!!!!!!!!!!!!
Muth
For every security measure there’s a counter measure, and for every counter measure there’s soon a new exploit – I’d simply suggest people open a new window, and not a new tab, for anything that’s sensitive . . .
intel_chris
@rage — maybe it wouldn’t catch you. That’s good. Would it be good enough to fool somebody sometime? I think so. To wit, people have been known to be fooled by phishing emails with obvious selling and grammar errors. Moreover, the script is designed to run after a period of inattentivity, meaning the user’s mind was on something else. So, if you are distracted having been doing something else for 5 minutes and you came back to your browser wanting to send a mail and you found gmail on the browser but it was logged out, would you never just login? Now make yourself a typical user (especially one not exceptionally tech savvy) and one who gets logged out of gmail regularly and has to log back in. Do you think in that case, your reaction will be that this is a phishing attack?
Honestly, I was reading the article and had to do something on my other laptop for a bit and I came back wanting to do something else and saw the gmail login on this laptop. Did I remember I was reading about the phishing attack? No, I was thinking about what I had to do. It was not gmail, but still it did fool me for a few seconds, as I went to close gmail since it wasn’t what I wanted. Oh, and it wasn’t really gmail, it was this proof-of-concept. So, am I convinced it might convince someone else? I think the answer to that is obvious.
Remember phishers are playing the lottery. They know every ticket isn’t a winner. They just hope once in a while they win enough. Would a script like this be good enough to get some people to give up their passwords some times? It was almost good enough to get me to do so.
nexpo
Hi, i visit this website for check new Phishing Attack, but stil nothing. I use ubuntu 10.04 and google chrome web browser. Thats means i’m away from this threat?
David Regev
This could be taken as an argument for reducing the separation between the URL and the page title. More specifically, the problem is that the domain and the title are not together, so people often miss the former, since the latter is what’s important. Suppose, however, if the domain and title were usually combined, as such:
There would then be a greater chance of noticing this forgery:
Mashable!
This post has been featured on http://mashable.com/2010/05/25/tabnabbing-phishing/
The Pontificator
Yeah, tried it on my Mac with four different browsers:
Safari: Exploit successful
Firefox: Exploit successful
Chrome: No exploit
Camino: No exploit
Carl
It didn’t work on my firefox browser with noscript installed.
Until I allowed scripts on your site that is.
I’ll try it on chrome next…
Lava Kafle
Wonderful best practical example of phising attack , thanks
justin
i tried this on the latest version of opera 10/53 and the icon your are talking about doesn’t change.
i have tested it twice and still no icon change.
(win7 ultimate x64)
although my opera executable folder is in the correct “my programs” folder i am using a portable usb version (i placed it in my programs for my own purposes)
you should be able to produce the same results.
just another reason why i use opera!!!!
Black
Use NoScript and the likes and you will be fine from most JS evils! :-)
Tjerk
IE8 is vulnerable too, chrome 5 is not
Pieter
Hello Aza.
I use Chrome 5.0.375.55 beta and the tab with your website remains intact, even after minutes and minutes of idleness.
Why does Chrome protect against such attacks and FF does not?
best,
Pieter
Aza Raskin
Many people have reported that the attack doesn’t change the favicon in Chrome. This was due to a bug in Chrome which has been fixed in the version 6.0.408.1. Chrome is fully susceptible to this attack.
keteflips
NoScript + Adblock Plus dude….
Yoram
If you install CallingID Toolbar you are protected. CallingID Toolbar includes a real-time protection that automatically detects trying to type a password in a suspicious site and warns you before submitting the password. Moreover CallingID site protection guarentees that if you are trying to submit the password that you use to login to a “CallingID Protected Site” to a different one you will automatically get a warning to protect you from disclosing your password to a phishing site.
metusalem 2
Very nice to hear how great and safe Firefox is. But after over a year of the ever unfixed and endlessly annoying ” cannot find server” bug, together with FF not loading images properly , the increasing startup slowness…I finally switched to Chrome. I loved FF, but it annoyed the hell out of me.
Why don’t you just FIX it once and for all, thousands of people are still complaining about the “cannot find server” bug… Chrome is lightning fast and far more efficient, and I stopped caring how safe and blah FF is when it never works as it should.
Heiner
I have tried on Chrome 5.0 on Ubuntu 64 bit and it happened after long time for it and working with some of the tabs
Tungsten
This is one of the things where NoScript saves you, this page does not change at all in my browser ;)
Ivan Ičin
Ah, don’t forget on using NoScript add-on to reduce such problems.
Jason Lancaster
Wow, smart and scary. Good job bringing this to everyone’s attention!
mayjune
Wow! Old wine in a complete new bottle!!
I am soo impressed by this new age thinking of hacking!
So simple, so elegent and yet so powerfull. Makes me think of other things that can happen in simple ways like this with a little twist… awesome!
FrankInTX
Using Chrome, it did change the tab title and page content but did not change the favicon.
Geoff Hart
FYI, the script on your site also works in the latest version of Safari for OS X, even though I wasn’t using tabbed browsing. That’s kinda scary when you think about it.
pierre
works also with safari…
frightening !
thanks for the tip
djz
I just tried this by accident – not going to another tab, but opening a full-screen chat window. Why’s it limited to only tabs? if I minimize a browser or use another window for a while, then return, the attack also works.
Kevin
It works in IE8. how easy would it to hide something like this in a greasemonkey script?
TechLady
Wow and Yikes at the same time. It even worked with my Yahoo toolbar tabs, YIKES.
As a web-designer this disgusts me!
Jitendra A
Seems this does not work on Google Chrome!
Tausif
I guess this attack wont work on IE6 since it does not have tabs :D
Long live IE6 ;D
Andrew
Very interesting PoC, not really a way to combat this one is there?
Michael Diamond
For once Yahoo was ahead of their time then – I assume their customized login page thing will really help fight this. Scary vector though!
Sean
I cannot believe that you nor any of your users never thought about URL spoofing through javascript. This coupled with spoofing of the URL in javascript would fool almost ANYONE – no matter how careful you are.
ingvar
Your crack doesn’t work on my firefox.
Mozilla/5.0 (X11; U; FreeBSD i386; sv-SE; rv:1.9.1.9) Gecko/20100416 Firefox/3.5.9
With noscript.
Commonus Sensicus
Well of course, but other than skilled Internet users (who might also detect this attack by other means like a mismatched URL or lack of SSL) who uses NoScript?
Juan
In chrome under linux it works, favicon included.
Thorsten
Does not work at all… The site keeps as it is… No gmail or whatelse login appears when chageing to another tab, even after minutes of waiting…
l104693
This is Great! One of the most impressive phishing attacks i’ve seen!
Security
Excelent info….this suplantation of web..perfect…
Clanggedin
This is absolutely, totally bada$$!
pigpromoter
It doesn’t change the favicon in Opera. Still… I can only say WOW.
brianlj
In Opera 10.53+ neither the tab’s favicon NOR the tab’s pop-up thumbnail change.
Also, if you are using Visual Tabs, that display doesn’t change either.
Only the tab’s title changes.
Martijn
Looks like flash elements are on top..
http://twitpic.com/1ru7g0
AluminumHaste
This is easy to prevent, simply run with NoScript plugin and you are safe.
AluminumHaste
lol I allow just the azarask.in domain in NoScript and your website changed right before my eyes to the Gmail login window while I was browsing the comments.
jarncrig
At least in nightly Dev Chrome 6.0.408.1 the CSS History miner leak is already fixed.
That is to say the CSS history leak is also no longer possible Dev Chrome and Safari nightlies.
gary
This is a devious instance of a whole class of phishing schemes to get someone to use a fake web page. A general solution might work like this:
1. Create a list of “real” sites.
2. The browser presents a dramatically different look when at one of these identified sites. Not just an icon or small change, but change the color scheme, display in large text on the title bar, etc. There could be a visual action when the focus is place on a password box. The browser would have to make sure that these looks are not programmable by a script.
At first glance, #1 looks impossible. But the list does not need to be complete, or even close. Phishers are looking for popular sites (FB, gmail, big banks, etc.). A list that just took the 500 most popular sites would make phishing much less worthwhile. Popularity should be based on a long period of time, so someone can’t trick their way onto the list. How often does a phisher have a top-500 web site?
The feature would need to be described carefully, to not imply that those not on the list are bad sites. It could just be called the “top sites” feature, but users would recognize if gmail or their bank site were suddenly not on the top sites list.
demo
That is genius!
I also noticed as i went for a quick smoke, came back after minimizing the window, i noticed this page had changed to the gmail spoof.
Thanks for the heads up, i always knew tabs were going to be a bad thing sooner or later :o
Josua
Arg.. my little sister is in danger…
jay
thanks for the knowledge
Anonymous
Just a little thought…
Its actually very simple to write a HTTP sniffer to listen on port 80 that can get and alter the webpage source before it reaches your browser. All you would need to do is change the action of the submit button to run a pretty little php script or something that will dump that data into your own database.
This is kind of a scary thing, nobody would even be able to tell the difference, the url would stay the same, the page would look exactly the same, etc.
Andrew
I use LastPass to store and input passwords. Is it possible to trick the extension (Firefox) into thinking this is the actual GMail page, and autologging in?
Roberto
Hola Master
From Peru…
I need to know a password of a gmail account
alnusaaqp@gmail.com
i can pay to to you the disturb
Eitan Adler
I have a version of this attack that does not require javascript to be enabled at
http://blog.eitanadler.com/2010/05/tabnabbing-without-javascript.html
Gakk
This tabnabbing without javascipt worked on iPad also…
Ron Payne
Disn’t even bother my Firefox as I make a choice as to accept cookies or turn on JavaScript on a site. Followed instrutions and came back to same page.
Ron
Gakk
It doesn’t seem to affect Safari on iPod, but I guess this might be because here the tabs are suspended/paused when i navigate to another tab?
Gakk
Neither iPad is affected…
Gakk
Eitan Adler poested a version what don’t require javascipt, and Safari on iPad was affected by that version :-/
http://blog.eitanadler.com/2010/05/tabnabbing-without-javascript.html
Danking
Noscript :)
Ahmad Mushtaq
This is awesome!! Gonna try on my friends!!! ;)
Thanks for such a great info…
wweeks
Realize however that with addons such as NoScript this attack won’t work.
Boudewijn
Wow, this is serious!
Erik van Eykelen
Our company is working on an XPI that will try to counter tabnabbing. It’s a side project but we’re hoping to release something soon. I’ll post a link here once it’s released.
Aza Raskin
Looking forward to it.
raj
It may work with people who use lot of popular services, like Gmail, Facebook and so on. If I don’t use any of these, I would be rather surprised when I suddenly find a Gmail tab in my browser. What does it do here?
And it is a good habit to work like this: log into a service (eg. online banking), do whatever you have to do there, and then immediately log out and navigate to another site. Even if someone later fakes the banking site in one of your tabs, you *know* you are done working there, so this site has no reason to appear.
Gil
WHAT!!! You have just provided a link to the source code to make it easy for Bastards out there to do this ???
Mike
The favicon in the address bar isn’t changing in Safari 4.0.5
Bart
Mmmm…
On Safari, neither it does change favicon, or the URL of the web site.
Yeah, javascript can do a lot of evil stuff, like a knife does… so what ?
Johnathan Pulos
Wow!!! Just amazing how people come up with these attacks. Great work in catching it.
Mike Santagata
Damn, Aza!! I was typing up comments and I hesitated a little while taking a phone call and just as I was getting ready to click [Submit Comment], your page auto-refreshed and showed the GMail login screenshot!!
and I lost all of my comments!!! :-(
I’ll try again…
Is this attack already occurring or are you just warning us that it could happen? And wouldn’t correct terminology be TAB-NAPPING -as in a tab that was kidnapped?? Just wondering …
Mike Santagata, Network Administrator
Gebhardt & Kiefer Law Firm — http://www.gklegal.com
Sinani201
I’m using the latest dev build of Chrome, and the title and favicon of this page changes, but the page gives me the broken image icon instead of Gmail.
rocraacker
http://www.azarask.in/projects/bgattack.js this is were the trick is :D
rocracker
http://www.azarask.in/projects/bgattack.js nice trick dude :D
Iry
The Gmail page loaded while I still had it on the current tab because I was typing something in Firefox’s quick search box…
Richard Clark
For the vaguely technical, a defense against this is reasonably easy. Both firefox and the latest Chrome will let you run a custom script ona given URL, using Greasemonkey.
I have one, for example, that runs on https://www.google.com/account/* and changes the background and styling of the page in a custom fashion. Your gmail login page looks nothing like mine.
The same tactic is applicable to all kinds of things where people might attempt to fake you into doing something with a familiar public view.
Josep
This info is quite valued and interesting
Thank you so much for sharing with the community
Thanks honestly
Thomas Costick
Seems to take more like 60 seconds for the effect. Happened while I was on this actual tab.
Chrome 5.0.375.55
WinXP SP3.
Karen G (BC)
I wonder if NoScript has this problem solved….. I have NoScript enabled on this site, and when I clicked on to another tab for over 5 seconds, nothing happened. I know I just got a NoScript update in the last couple of days. It sure is a scary phishing attack.
Michael
I’m not code-literate – following Richard Clark’s suggestion, would a one-time distinctive customizing of my web email alert me if someone tried this? or would it be simple for my customization to be copied on the phishing page?
Lepper
I’m using Opera 10.50/Windows 7 and the favicon was still your blog’s one after the page ‘turned into’ GMail.
Richardus
It didn’t work with Noscript (Ver. 1.9.9.81) on. Once I temporarily allowed this page I got the Gmail image.
One interesting thing is, if a site convinces a user to turn off whatever filter they’re using (to watch a video or other similar content for example), then this kind of attack will be successful…
Olga Lednichenko
thanks for educating us on such nefarious attacks
regds
olga-lednichenko
RG
Funnily enough, the Colourful Tabs Addon for Firefox is good way to gaurd against this type of attack.
SH
Thats’a scary one…
Maybe browsers could restrict background changes to things within the same domain, ie setting a form to direct a user to bankofamerica.fake.com would be blocked while away (or at least flag a warning) because it is not in the domain “mysite.com”.
Admitidly, this may stop some dynamic things from playing nice but, as with all security measures, there’s always a trade-off.
xemmy
Pretty creative :).
Since i surf with NoScript Plugin, the trick doesnt work, unless you allow the Page.
But still pretty interesting.
corrosion
the demo page is not working
P.S::using ff with no-script latest version.
Jason Martin
I see where you’re coming from, but I noticed something interesting; this is whenever the window looses focus, not just when you switch tabs. I noticed this because you mentioned that a certain version of Chrome isn’t susceptible. Curious, I checked to see what version of Chrome I was using. That simple act of opening the About window in Chrome triggered the page to think you had switch to a new tab, and you could visually see the page change, as the About window does not completely cover the website. This doesn’t take away from the validity of this kind of attack. It merely means that someone would have to code the attack differently to take into account this possibility, which, if I remember correctly, isn’t possible to do in code.
Jason Martin
To add to my comment, even switching to another app that doesn’t completely cover the web page (like, say for example, Finder) will trigger the page to change, which should serve as some kind of warning for the user.
Stardance
FWIW, I went to the Gizmodo link about Unicode Domain Name attacks, to which you referred, on a new tab, of course. From the comments that have been posted there by readers, the use of Cyrillic and other non-Latin writing (such as simplified Chinese) cannot be used to create the Unicode Domain Name attack that Jesus at Gizmodo described. He refers to a page on the Times Online (now a 404) “via Mashable.com” — a link to an article there which has the byline of Christina Warren that apparently was based upon the Times Online report.
That “attack” seems to be a nonesuch. However, if your website page, where I am writing these remarks, can be used to test tabphishing, then something seems amiss. I spent a while reading the articles on those websites on their respective tabs, and the Firefox 3.6.3 tab for this page never changed.
Since I do not have a Gmail account, maybe that is why your web site does not execute the attack. Of course, I would be more than a bit mystified if a GMail tab replaced the content for another open tab.
filippo
Molto interessante.Oggi bisogna essere informati sempre anche se sembrano banalita’
solak
I am extra glad that I use 1Password to store my authentication information. Since the URL would not be in the correct domain (even if it looks as if it is), hitting command-\ would not fill in the name and password, and my suspicions will now be aroused enough to investigate.
Thanks for pointing out that I should do so, since I might formerly have simply thought that this kind of attack was *yet another* URL variant for which I needed to train 1Password. I’m sure that other password vaults provide this benefit as well.
wonght
My avg picks it out before the attack went thru
César
Mine too!
akJones
Whoa…thanks for posting this! It makes me not regret my paranoia in tediously re-navigating to a page instead of just “logging in again” whenever I have a failed login or session timeout (I know, I’m a noob…there are probably some more efficient ways out there). Of course Firefox & NoScript helps…
__SENATOR__
hi. how can i make some page like this? i want to use this,
Simon
Having spent the last 6 weeks or so retrofitting security to vintage application that failed penetration testing by a 3rd party pen testing company, I found this an interesting/informative artical – thanks :-)
Roberto Felix
Wooow, you are a genius!
eve isk
Very good work!
Thanks!
Kaysan
I tried this using Safari but I didn’t get the tab change? User error? Because Safari was used in the demonstration? (Using Windows Vista w/ Safari)
Feedback from azaaza would be appreciated (via my email)
Thanks!
Keithing
Hy,
nice trick, but it doesn’t work so easy in Opera.
First you need in all browsers the Javascript functionality enabled – use “NoScript” for Firefox to prevent this.
Second, the favicon does not change in the latest version of Opera.
Second, the tab preview feature of Opera shows a different picture which makes it a tad harder.
Still you are right, this can be very harmful.
Ritu Sharma
thats very help full.
Del
In addition to spending a lot of time and effort in trying to find solutions to these computer attacks, why do we never ever hear of these assholes being caught and their hands cut off at the wrists??
Their ability to commit self abuse has far far less priority than screwing up hundreds of thousands of computers.
24needs
hey something attracting in you post.. i think its not working in opera..
Good work
Thank you for sharing with us
Thank you
24needs
Guilherme
que coisa !!
Mariposa Plexippus
your tricks don’t work if noscript is installed
Yo Ma Ma
my freind emailed me -
“Did you know that the link in your FB message about
tab napping is identified by AVG as containing nefarious
javascript code?”
Misacek01
Hi,
just tried this out, and it doesn’t work. I have Firefox 3.6 with the latest noscript enabled, but the phishing attempt was blocked by the Windows Vista web shield, or whatever its name is. It even identified it correctly as tabnabbing…
Jim
The first thing I noticed on the “exploit” page was that the free space number was not changing. Was this intentional or was it an oversight?
-Jim N
Anton
But this not work on IE :)
Junadi
it can be detected by using common sense… so simple, always watch at the url
and you have written a very clear and understandable page
Buzz
Doesn’t affect Opera, Favicon doesn’t change. tested in 10.60 (and the website mentioned in chrome bug report is working fine in Opera, so it’s not a bug).
Actually if the phiser managed to change the URL in the address bar, this method will be almost flawless. Nice find, and btw I like your site design.
Sequoia McDowell
+1 to everyone who said Opera Wand and FF Secure Login. If one religiously used one of these (hotkey to log in) and took the time to look very closely (just that once!) when adding a password, this attack wouldn’t be very affective.
Then again if you’re like me and say “huh, must not be working; I probably saved this pass on another browser” and enter your password, you’re out of luck!
The Rook
“Tab Nabbing” isn’t a new attack. It was discovered by PDP from GnuCitizen back in 2008:
http://www.gnucitizen.org/blog/hijacking-innocent-frames/
jeflev
ugly: this attack JUST HAPPENED TO ME while reading the description of the attack: the page (and tab) changed to ask for my Gmail login; weird and awful; I now feel unsafe everywhere I put in a username/password …
So …. having read many of the comments …. WHAT’S THE SOLUTION???? HOW DO WE PROTECT OURSELVES????
Ben
Wouldn’t OpenID be a better solution than having browsers remember “who we are”? If your authentication is in the browser, you’re limited to one browser, and you can’t let anyone else use it. OpenID lets people use multiple browsers and share computers, as people are wont to do.
Francisco Pereira
Good day sir
While opening this page my AVG antivirus, notifies that a file is infected with tabnapping, is it normal.
best regards
Niek
Resetting the window.onblur event will remove any phisingcode I suppose?
Varinder Akash
There is a quote from book ” Computer Vulnerabilites” -In fact, as many different security measures that have been
invented have been circumvented almost at the point of conception. And it goes on. Any browser or technology that is being developed shall have some vulnerability, however that can be patched , but you cant patch a human’s psyche , We as humans will always be vulnerable to deception of some kind at any level.
robinsondemitrius4
great post and i like this,,,,,
Like most web developers or SEO professionals, I use a vast array of tools to get the job done. I use a combination of desktop and web applications, some purchased and some free. Everyone I know has downloaded a free copy of Mozilla Firefox, but few realize that by installing some of the 1,500 free extensions they can eliminate the need for most of the other applications they currently use. Below are my 13 favorite extensions for web professionalshttp://www.techhairball.com/
SR
I couldn’t get it to work in FF 3.0.19 by switching tabs. Then I opened the Tools menu and, while I watched it happening, the page was replaced by the Gmail image. Then I couldn’t get it to happen again.
qwert Tom
great post and i like this blog…
When you regain your woman’s love and affection, it’s not going to be by continuing to be a beta male who constantly kisses her ass. Nor is it going to be by calling her and texting her 18 times a day. (That may work in films, but in real life it just drives her away.)This powerful material is only for you if you’re fed up with the loneliness and ready to drop your ego and get serious about getting your baby back into your life.
http://www.exbacktip.info/index.htm
kn33ch41
Clever and succinct!
Steve Coverdale
Thank you for pointing this one out.
Les Potter
I like to “middle” click on links on a page to get a new tab. Your demo is cool, but it thinks your page is no longer visible in fact it is. So, it changes before my eyes in about 5 seconds. This is probably a very simple fix to tighten up the behavior.
Quinn C.
This is scary.
This totally caught me by surprise. I opened this to read later, and navigated to a different tab. Then later I navigated back and was like “What the…”. Then I looked up and saw the URL. Scary.
Fernando Echegaray
I was exposed yesterday to the attack. I really don’t know from wich website they nabbed my tab, but hey switched my yahoo account log in, at the same time they were able to chat using the mail chat, trying to get me to enrroll in Live Web Cam site. I talked with the girl live, that’s when I noticed something wrong about the look of the tab.I clicked on the tab to see the source the it said that was verified by equifax! I closed firefox and changed my passwords using diffrent browser. There in yahoo also I noticed that people been trying to get me to allow them to chat, to try to do the Cam Scam.. I had the latest Firefox, I uninstalled…
martin
Not if you use NoScript. Thanks for the heads up.
Ithil26
I’ts curious AVG detects your experiment as threat.
I’m really protectec with avg
Wolf Kirchmeir
What makes this attack so insidious is that it’s completely cross-platform. Having a “more secure” OS doesn’t protect you.
wolf k.
Cybe R. Wizard
The re new feature when changing to another tab didn’t work here.
Ubuntu 10.04 updated yesterday.
Firefox 3.6.8 Mozilla Firefox for Ubuntu Canonical-1.0
NoScript 2.0.1
Dylan Mahon
This attack doesn’t work at all with SRWare’s Iron.
Dan Hoyt
Another good way to protect against this attack? Try a Firefox add-on called NoScript. It forbids every new domain from running javascript. With your trusted websites, you can allow them permanently and with potentially untrusted websites, you can allow them only temporarily.
Mark
Fascinating!
Very informative as well. Glad i use firefox!
Joseph Crawford
I believe you could also change the address in the address bar to resemble google mail. something like http://mail.google.com/#
Facebook does this on their image slideshows and I believe all you have to do is update the address on the event using document.location.href and apply a # to the URL, you do this so that the page will not refresh, you can use the anchor element as a marker.
Joseph Crawford
More about changing the URL using AJAX to make this even harder to notice: http://ajaxpatterns.org/Unique_URLs
Sebastian Campbell
Amazing
unnex
yeah, that’s why the internet is so uncertain. because people always some wannabe
with their methods and come to think that must stand as a threat. without having
to investigate the matter -.-
see here: http://www.file-upload.net/download-2820724/7a8ct87ac.wmv.html
gucci belts
The basis of its investigation indicates that mens belts they operate cheap gucci belts on a sustainable path cheap louis vuitton belts for men of poverty, cheap desiger belts job security gucci belts on sale and low wages. The Department louis vuitton belts cheap for Work and Pensions, said, with five billion people return to work undertaken. The charity said that about one-fifth of the poverty and again and again where people escape from poverty on a temporary basis.
Steve
AVG Link Scanner blocked it. Using safari on an iMac.
1
with proxo running, this worked once i turned on js and imgs
i don’t think the favicon changed though.
Deepak
Not working, nothing changes. I don’t see any errors in javascript console either.
Google chrome 6.0.472.62 on Ubuntu 10.04.1 Lucid Lynx.
Nick
I also tend to be suspicious when I see login/password fields and so sign of SSL.
On Firefox 3.6.x, I’m accustomed to seeing SSL-encrypted pages displayed with a blue badge (or green for EV) in the address bar (I can’t bring myself to use the word “awesome”), as well as a padlock icon in the status bar.
A hack like this cannot change the browser chrome to fake that, can it?
eve isk
great article.ty
supraskytop
What more know about the story?supra footwearor ?
my name is supra ,when i land on your blog,you atricle is so good .i like it so much….
Khan
Hi..
Very nice
albino
I’ve just created a somewhat similar attack; it adds in URL hijacking for a less obvious (but more suspicious) attack:
chronofeit phishing
@Nick The attacker can make the URL bar green by making their site SSL.. Aza probably didn’t bother because it is just a proof of concept but a real attacker would.
Dave
The quick reference to look-alike unicode domain names should be removed. That is not real. You cannot use russion unicode to fake a .com name; it would have to be a .ru domain. The rules for unicode domains require the character set to be a primary for that tld.