 |
Even with this somewhat more restricted scope, we find there are still a very large number of possible protocol ambiguities to address. Consequently, it behooves us to develop a systematic methodology for attempting to identify and analyze all of the possible normalizations. The methodology we adopt is to walk through the packet headers of each protocol we consider. This ensures that we have an opportunity to consider each facet of the semantics associated with the protocol.
For each header element, we consider its possible range of values, their semantics, and ways an attacker could exploit the different values; possible actions a normalizer might take to thwart the attacks; and the effects these actions might have on the protocol's end-to-end semantics. Whilst our primary intention is to explore the possible actions a normalizer can take, the exercise also raises interesting questions about the incompleteness of the specifications of error handling behavior in Internet protocols, and about the nature of the intentional and unintentional end-to-end semantics of Internet protocols.
For reasons of space, we confine our analysis here to a single protocol; we pick IP (version 4) because it is simple enough to cover fairly thoroughly in this paper, yet has rich enough semantics (especially fragmentation) to convey the flavor of more complicated normalizations. In § 6 we then present some particularly illuminating examples of TCP normalizations. We defer our methodical analysis of TCP (and UDP and ICMP) to [4].
Note that many of the normalizations we discuss below appear to address very unlikely evasion scenarios. However, we believe the right design approach is to normalize everything that we can see how to correctly normalize, because packet manipulation and semantic ambiguity is sufficiently subtle that we may miss an attack, but still thwart it because we normalized away the degrees of freedom to express the attack.
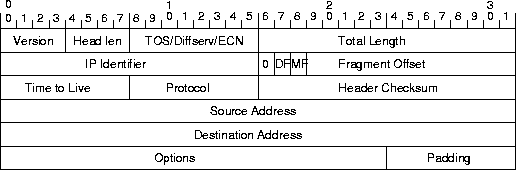
Figure 3 shows the fields of the IP packet header. For each field we identify possible issues that need normalization and discuss the effects of our solutions on end-to-end semantics. The reader preferring to delve into only more interesting normalizations may choose to jump ahead to § 5.1.
![\framebox{
\begin{minipage}[h]{0.45\textwidth}
\small
\framebox{\textbf{Version....
... pass packets with IP version fields which the NIDS
understands.
\end{minipage}}](img6.gif)
![\framebox{
\begin{minipage}[h]{0.45\textwidth}
\small
\framebox{\textbf{Header l...
...s indicates
options are present. See IP option processing below.
\end{minipage}}](img7.gif)
![\framebox{
\begin{minipage}[h]{0.45\textwidth}
\small
\framebox{\textbf{Type Of ...
...ffserv-RFC} and explicit congestion notification \cite{ecn-RFC}.
\end{minipage}}](img8.gif)
![\framebox{
\begin{minipage}[h]{0.45\textwidth}
\small
{\bf Issue:} The Diffserv ...
...g them is safe. Otherwise,
clearing them breaks use of Diffserv.
\end{minipage}}](img9.gif)
![\framebox{
\begin{minipage}[h]{0.45\textwidth}
\small
{\bf Issue:} Some network ...
...rom benefiting from avoiding packet
drops in some circumstances.
\end{minipage}}](img10.gif)
![\framebox{
\begin{minipage}[h]{0.45\textwidth}
\small
\framebox{\textbf{Total le...
...Effect on semantics:} None, only ill-formed packets are dropped.
\end{minipage}}](img11.gif)
![]()
![\framebox{
\begin{minipage}[h]{0.45\textwidth}
\small
\framebox{\textbf{Must Be ...
...tocols should degrade gradually in the presence of
difficulties.
\end{minipage}}](img13.gif)
![\framebox{
\begin{minipage}[h]{0.45\textwidth}
\small
\framebox{\textbf{Don't Fr...
...network
environments, these are unlikely to be serious problems.
\end{minipage}}](img14.gif)
![\framebox{
\begin{minipage}[h]{0.45\textwidth}
\small
{\bf Issue:} Packets arriv...
...ackets.
\par {\bf Effect on semantics:} None, ill-formed packet.
\end{minipage}}](img15.gif)
![\framebox{
\begin{minipage}[h]{0.45\textwidth}
\small
\framebox{\textbf{More Fra...
...assembled packets if the normalizer starts to run out
of memory.
\end{minipage}}](img16.gif)
![\framebox{
\begin{minipage}[h]{0.45\textwidth}
\small
{\bf Issue:} Packets wher...
...r {\bf Effect on semantics:} Packet is ill-formed, so no effect.
\end{minipage}}](img17.gif)
![% latex2html id marker 681
\framebox{
\begin{minipage}[h]{0.45\textwidth}
\small...
...e the
normalizer from the point of view of the search algorithm.
\end{minipage}}](img18.gif)
![\framebox{
\begin{minipage}[h]{0.45\textwidth}
\small
\framebox{\textbf{Protocol...
...ontain
well-known protocols, such as those the NIDS understands.
\end{minipage}}](img19.gif)
![\framebox{
\begin{minipage}[h]{0.45\textwidth}
\small
\framebox{\textbf{IP heade...
...ts with incorrect IP checksums anyway, the
issue is likely moot.
\end{minipage}}](img20.gif)
![\framebox{
\begin{minipage}[h]{0.45\textwidth}
\small
\framebox{\textbf{Source a...
... network, the normalizer might be configured to drop the
packet.
\end{minipage}}](img21.gif)
![\framebox{
\begin{minipage}[h]{0.45\textwidth}
\small
\framebox{\textbf{Destinat...
....
\par {\bf Effect on semantics:} None, destination
is illegal.
\end{minipage}}](img22.gif)
![\framebox{
\begin{minipage}[h]{0.45\textwidth}
\small
\framebox{\textbf{IP optio...
...h
site-specific policies controlling the normalizer's operation.
\end{minipage}}](img23.gif)
![\framebox{
\begin{minipage}[h]{0.45\textwidth}
\small
\framebox{\textbf{Padding....
...ar {\bf Effect on semantics:} None, field is explicitly ignored.
\end{minipage}}](img24.gif)